Rapid Security Response: Fractureiser
Many popular Minecraft mods have been infected with Fractureiser, a virus that can steal sensitive data such as logins and cryptocurrency.
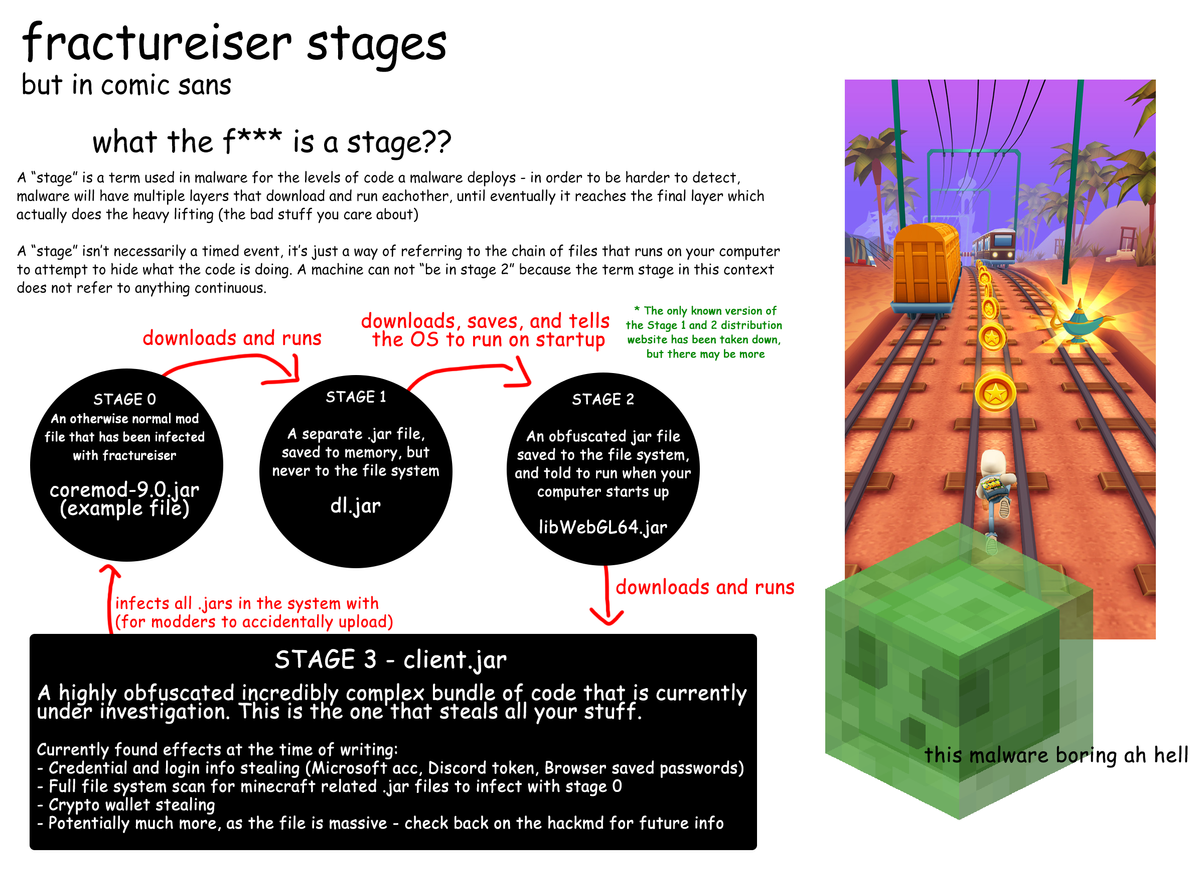
I Saw a Pop-Up on My Device, What Does It Mean?
Fyra Labs issued a Rapid Security Response for Fractureiser, a virus that can steal sensitive data such as logins and cryptocurrency. The security response is a small program included with all Minecraft related packages distributed by us. This program checks for Fractureiser after a software update, removes the malware, and shows the popup if it's found.
We care about your privacy, no data used in the detection ever leaves your device, and Fyra Labs can never see your files.
If you saw a pop-up: Fractureiser was found and removed from your device. This doesn't mean you are safe. Please make sure to review the "I Removed Fractureiser, What Do I Do Now?" section of this article.
What Happened?
Developer accounts on Curseforge and Bukkit were compromised by malicious actors. These actors added malware, called Fractureiser, to mods published by the compromised accounts. The updated versions of these mods don't show up on the Curseforge or Bukkit websites and are only visible via the API.
What Mods are Infected?
As of June 7, 2023, the following mods are known to be infected
CurseForge:
- Dungeons Arise
- Sky Villages
- Better MC modpack series
- Dungeonz
- Skyblock Core
- Vault Integrations
- AutoBroadcast
- Museum Curator Advanced
- Vault Integrations Bug fix
- Create Infernal Expansion Plus (Removed from CurseForge)
Bukkit:
- Display Entity Editor
- Haven Elytra
- The Nexus Event Custom Entity Editor
- Simple Harvesting
- MCBounties
- Easy Custom Foods
- Anti Command Spam Bungeecord Support
- Ultimate Leveling
- Anti Redstone Crash
- Hydration
- Fragment Permission Plugin
- No VPNS
- Ultimate Titles Animations Gradient RGB
- Floating Damage
How Do I Know If I Have Fractureiser?
Automatic Checks
If you installed any Minecraft packages from Terra, you will see this popup if Fractureiser is found.
Make sure you update your device, this popup will not appear if Fractureiser is not found.
Running the Detector Manually
If you'd like to double-check our work, or don't use Terra, please use this script provided by the PrismLauncher team:
curl -fsSL https://prismlauncher.org/img/news/cf-compromised/check_cf.sh | bashThis command downloads and runs the script
The script can be found here. Please review it before running it on your device.
Common Signs of Infection
Look for systemd-utility.service in ~/.config/systemd/user or /etc/systemd/system/ and lib.jar in ~/.config/.data
How Do I Remove Fractureiser?
Fractureiser will be removed automatically by the detection script.
I Removed Fractureiser, What Do I Do Now?
Fractureiser was removed from your device, but that doesn't mean you're completely safe.
- Change all of your passwords (We recommend using a password manager to store your new ones)
- Keep an eye on what devices are signed into your account, remove any you don't recognize
- Move any crypto to an unaffected wallet
How Can I Stay Safe?
It's pretty simple:
- Check your computer for Fractureiser
- Don't install or update any mods
That's all there is to do.
How Do I Get Additional Support?
Fyra Labs is here to help. You can get in touch with our team in a few ways.
Ticket
We've created a special form to open tickets about Fractureiser. We'll get back to tickets within 24 hours.
Discord
You can join the Ultramarine Linux or Fyra Labs Discord servers to get support in minutes.
Send an email to [email protected], we'll get back to any emails within 24 hours
What Does Fractureiser Do to My Device?
Simply put, Fractureiser infects your copy of Minecraft, and uses infected game files to steal account logins, cryptocurrency, and other sensitive data.
Fractureiser works in stages, each one preforming a different part of the malware's task.
If you are easily bored, please refer to this infographic provided by the researchers:
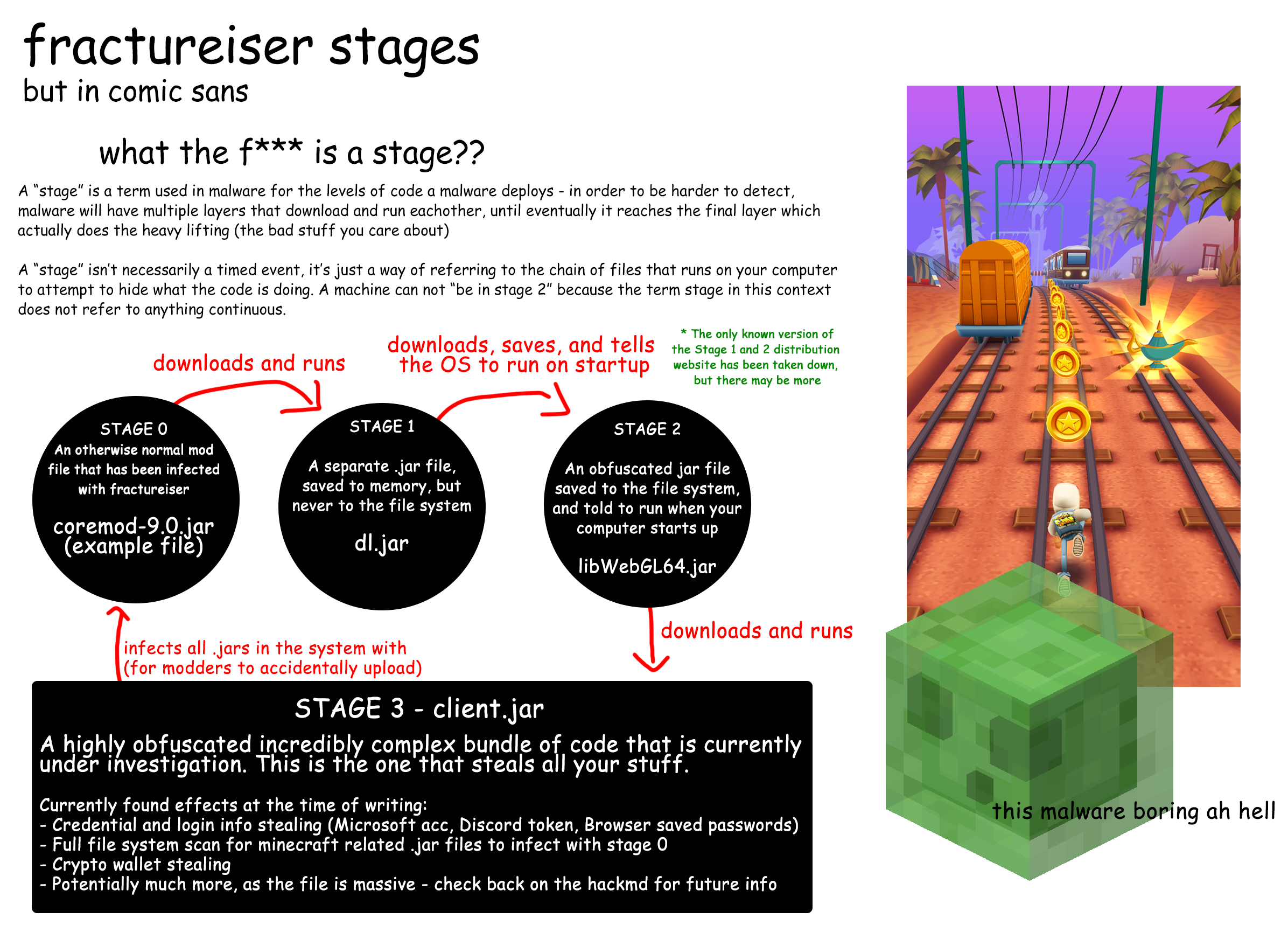
Stage 0
Infected mods install Fractureiser, and log it for the attacker.
Stage 1
The freshly installed malware checks for a system property called neko.run, if it's found, Fractureiser stops. Sadly this is not a reliable method of inoculation as Stage 0 downloads a new copy of Fractureiser every time and the search for this property may change in the future.
At this point, Fractureiser attempts to contact a server used for controlling the malware. Researchers are currently working with Cloudflare to get the server taken down.
After connecting to the server, Fractureiser downloads Stage 2, and sets it to run on startup by creating a systemd unit file in /etc/systemd/system or ~/.config/systemd/user. The latter does not work, as it calls for multi-user.target, which cannot be used for user units.
If your launcher is running as any user other than root, it's quite possible that the malware may not continue past Stage 1. This does not mean you are completely safe.
Stage 2
At this point, Fractureiser is established on your device, but hasn't started doing anything nefarious.
Stage 2 opens port 9655 (but closes it when JVM quits) and checks if Stage 3 is intact and up to date. It then hides Stage 3 with file attributes and launches Stage 3.
Stage 3
Stage 3, or nekoclient, is the true payload of Fractureiser, and what does all the stealing we mentioned earlier. It starts by infecting any other Java programs found on the device. Then it moves on to your browser, stealing cookies and session tokens, this is especially dangerous as it allows the attacker to bypass your password and Two-Factor or Multi-Factor authentication. It then replaces any cryptocurrency addresses in the clipboard with ones owned by the attacker. Finally, it steals Discord, Mojang, and Microsoft account credentials.
Browsers Affected by Stage 3 (Login Theft)
- Mozilla Firefox
- Waterfox
- Pale Moon
- SeaMonkey
- Chrome
- Edge
- Brave
- Vivaldi
- Yandex
- Slimjet
- CentBrowser
- Comodo
- Iridium
- UCBrowser
- Opera
- Opera Beta
- Opera Developer
- Opera GX
- Crypto
- CryptoTab
Launchers Affected by Stage 3 (Microsoft Account Theft)
- The Official Minecraft Launcher
- The Old Official Minecraft Launcher
- PrismLauncher (and PolyMC)
- Technic
- Feather
- LabyMod (< v3.9.59)
- Windows Credential Manager (Not a launcher, but stores Microsoft Accounts)
Attribution
Most of the information provided in this article is courtesy of the Fractureiser Mitigation Team. Thank you for your research.
Additional thanks to the PrismLauncher team for their fast response and creation of the detection script.
Affected Fyra Labs Products
- Terra 38
- minecraft-launcher
- prismlauncher - Terra 37
- minecraft-launcher
- prismlauncher
Terra Security Policy can be found here.

